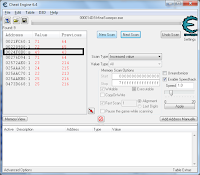
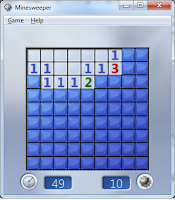
Take a look at the picture on the left, the screenshot was captured on popular windows game, minesweeper. Mathematically and logically impossible for a normal person to complete the game in 1 second.
The picture was not photoshop, it is a genuine picture.
I made this possible using cheat engine. Usually cheats are purposely developed along with original games but for games like minesweeper, no official cheat ever been created.
Using cheat engine, we can cheat almost any games with proper technique and some creative mind. We can win any game using cheat engine
1. Download cheat engine at
http://www.cheatengine.org/downloads.php and install it in your system
2. Open cheat engine ( use 64bit version if your OS is 64bit)
3. Open minesweeper games
4. Click on process explorer in cheat engine and select minesweeper.exe then click on Open
5. Leave minesweeper, don't start clicking yet. Click on first scan, value type all and scan type value between. Insert 1 to 50 . Now click your first tile. The timer begin counting.
6. As soon as the timer started (make sure before timer reach 50 or you'll need to reset the value between again) click on first scan again. it will find any address with the value between 1 to 50 and display the result on the left tab
7. Select increased value on scan type and click on increased value repeatedly until you see an address with an increasing value and have the same value a the timer. If result list become empty , repeat the first scan and keep trying.
8. Double click on the suspect , the address will be copied to the bottom tab
9. To test the suspect, tick on the rectangle beside the address , the timer shall freeze now
10. Double click on the value at the bottom bar and insert the value to change . I.e ; 0 then click OK. The timer now changes to 0 and increase to 1 then freeze.
11. Keep on playing and finish the game. You have successfully cheated the minesweeper game.
This cheat engine could be used on various other games that used the RAM for temporary storage. Also if you get creative, you could bypass the trial or demo software limitation using this method. I.e: 5 song per session, 5 minutes per session. All you have to do is get creative and never stop trying. I must repeat, you can win any game using this cheat engine.