Imagine that you are a supermarket owner with plenty of sections placing various type of products. Which do you prefer, a potential buyer that have various interests and browse through many sections or 100 potential buyer with 100 different interest go directly to their interest section?
In a world of blogging and online market, those 2 types of scenario actually present and greatly influence the performance of a blog or website. Now we need to understand the basics in measuring your site's popularity
Pageview
Pageview counts how many time your page is viewed. for example, a visitor land on your main page, that counts 1 pageview. Then he click on another post link , counts 2 pageview. If your site have 10 pages and he goes to all 10 pages, that counts 10 pageview.
Visit/Unique Visitor
Unique visitor counts every different person that goes to your website identified by their IP address. Ip address is unique. This is the most essential numbers to measure your site popularity
For blogger platform users, there is a blog stat function that shows how many pageview counts by day, week, month and all time but is it accurate? Didn't you realize that the pageview counts also add up when you refresh your page? Also listed in stat function are post view counts, traffic source counts and audience counts. Still the data is not sufficient to determine WHO are the visitor to your site, what type of person they are, what are their interests, how much time they stay on your site, how they come to your site and how they get out. Those are set of parameters that are very important to improve your site content and ad targeting. We need to use google analytics to access those set of parameters. Trained webmasters are very familiar with Google analytics but as a blogger or blogger to be lacking the webmaster's skills, do you know how to use analytics with Blogger.com? Read on guys. It is easy as a pie.
First thing first, head on to google analytics portal
here and sign in to google analytics. Use the same account as in blogger.com
After logged in, for first time user, you will be presented with some introductions on google analytics. Either follow the instructions or you can skip it.
Now go to admin tab, on account section(the leftmost). click on the dropdown list and select create new account.
Fill in the name of this new account, your blog url i.e http://learningtoolcheap.blogspot.com , industry category and reporting time zone.
Leave all those check marks checked and after finished with the form, click get tracking ID. Copy the tracking ID and paste it in notepad
At this point, analytics account setup had been finished, now head on to you blogger account, log in and go to your blog dashboard. Click on setting-other. In Google analytics section, paste tracking ID supplied in previous step in Analytics web property ID text box.
Now your blog have been integrated with google analytics. Google crawler will take some time to reach your blog. After an hour or two or in some cases 24 hour, the data will start showing in google anlytics. After logging in, you will see your account overview with some summaries of the data collected. Now click on your account to see its detail
You will be shown the site audience overview with its Sessions, Users and Pageview.
Click on audience-geo-location. Your audience location count will be shown here. In this example, the audience are mostly come from Malaysia
Click on audience-mobile-overview, you can see how many users use desktop, mobile and tablet to access your site. In this example, majority of them use mobile.
Let's dig deeper, click on audience-mobile-devices. You will see counts of each mobile brand your audience use to access your site.
This one is my favourite feature of google analytics. In-Page analytics. Click on behaviour-in-page analytics. Some chrome users will experience error in opening this item. Just click on load in full view
This feature will show how your audience behave in your site, how long they stay in your site, how many users are viewing your site in real time and what do they click on. This is very important in planning your ads and link placement. It also could give rough ads click count.
For this special function, google had developed a chrome extension that could show your site in-page analytics without going to google analytics portal. Get the extension
here and install it.
Go to your site and click on the analytics button to show in-page analytics.
Click the button again to turn it off.
In the example above, majority of the audience are using mobile device to access the page. It is essential to make sure the page performs well in mobile device browser. Do you need to buy all mobile device or let say borrow it from your friend to test the page? Absolutely no, don't have to do that. Just install mobile browser emulator chrome extension. Get it
here .
To emulate the mobile device browser, go to your site and then click on the 'm' button and select which device you would like to emulate. A new window will open will an emulation to your site in selected mobile device.
With those set of tools, you can customize your site and plan your content to cater every aspects of your audience behaviors and properties. Keep working on and use Google analytics for Blogger to grow your blog. Good luck



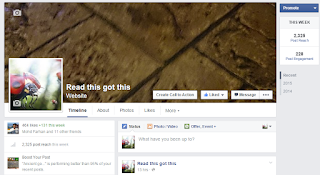 My page Read This Got This got 464 likes from merely 1 likes after running FB page likes promotion for 3 days on RM20.00 budget ~USD$5.00. The country and interest targeting was left to default option. Guess what, most of the page's fan are from Pakistan.
My page Read This Got This got 464 likes from merely 1 likes after running FB page likes promotion for 3 days on RM20.00 budget ~USD$5.00. The country and interest targeting was left to default option. Guess what, most of the page's fan are from Pakistan.  Looking into the pages insight, I realized that most of Read This Got This 's fan and reach are from Pakistan. So I tried to post something that looks a bit Pakistani to see if I could get more engagement but the result is still the same.
Looking into the pages insight, I realized that most of Read This Got This 's fan and reach are from Pakistan. So I tried to post something that looks a bit Pakistani to see if I could get more engagement but the result is still the same.
 Some evening, a friend of mine asked me if I ever have hacked a network or ever created a virus program or ever created a batch file that has the ability to crash a Win 7 system, my answer was no without ever seeing him in the eyes. Although I had done those before, my answer is always no because I don't want to be seen, unless I want to be recognized.
Some evening, a friend of mine asked me if I ever have hacked a network or ever created a virus program or ever created a batch file that has the ability to crash a Win 7 system, my answer was no without ever seeing him in the eyes. Although I had done those before, my answer is always no because I don't want to be seen, unless I want to be recognized. Gold bars reported to have been found i a Japanese WW2 war tunnel tunnel in a plantation owned by Sime Darby in Sabah, Malaysia. News spread out in social media including findings of gold bars etched with the word Sumatra , dated on 28.08.1941 and 999.9 However the truth on the news cannot be verified as none of the plantation's worker admitted the findings. Rumors said that all the gold bars had been taken by the workers hence no gold bar found Read More >>>
Gold bars reported to have been found i a Japanese WW2 war tunnel tunnel in a plantation owned by Sime Darby in Sabah, Malaysia. News spread out in social media including findings of gold bars etched with the word Sumatra , dated on 28.08.1941 and 999.9 However the truth on the news cannot be verified as none of the plantation's worker admitted the findings. Rumors said that all the gold bars had been taken by the workers hence no gold bar found Read More >>> Facebook has become more and more secure and is very hard to be hacked off to steal anyone's password. In one episode of a popular series, Leverage, they had come upon a person which us an old computer without any connection to the outer world and made hacking the computer to be impossible. Guess what, they hack the guy's mind. Literally, of course. Using the same idea, listed here 7 social engineering techniques to steal facebook password.
Facebook has become more and more secure and is very hard to be hacked off to steal anyone's password. In one episode of a popular series, Leverage, they had come upon a person which us an old computer without any connection to the outer world and made hacking the computer to be impossible. Guess what, they hack the guy's mind. Literally, of course. Using the same idea, listed here 7 social engineering techniques to steal facebook password. Let the victim use your laptop/PC with your chrome browser left open logged in with your google account. Usually people will only click the left most button on any prompt. If you got lucky the target will save their facebook account password in your saved password database
Let the victim use your laptop/PC with your chrome browser left open logged in with your google account. Usually people will only click the left most button on any prompt. If you got lucky the target will save their facebook account password in your saved password database